
What is Social Engineering?
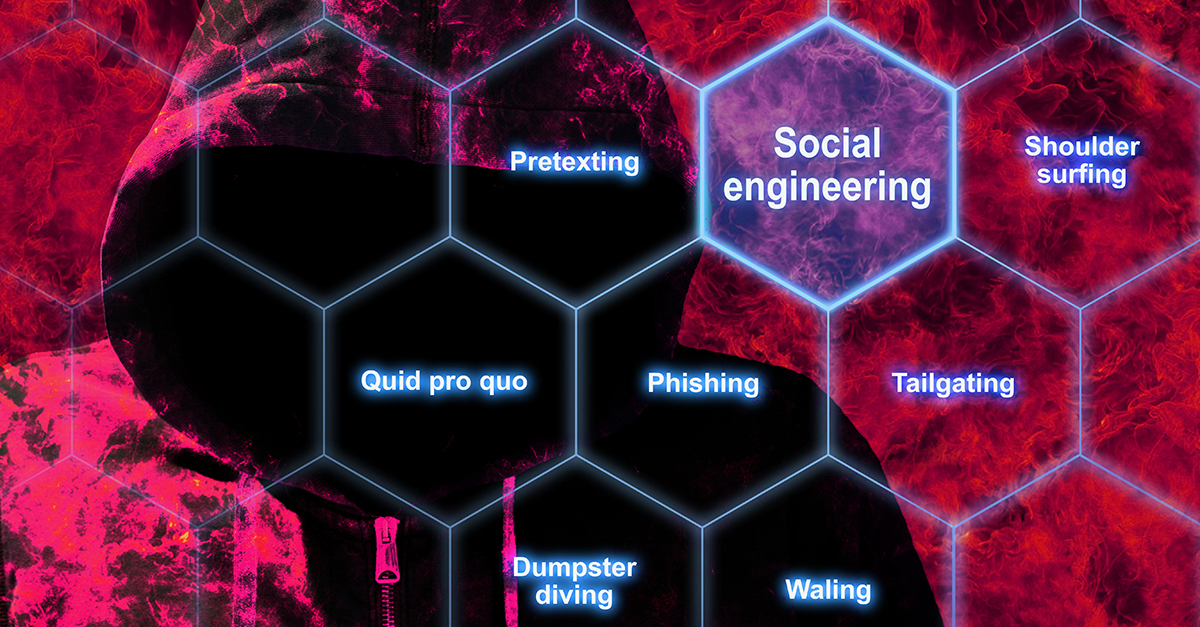
Social Engineering
Definition
Social engineering is a manipulation technique that exploits human error to gain private information, access, or valuables. In cybercrime, these “human hacking” scams tend to lure unsuspecting users into exposing data, spreading malware infections, or giving access to restricted systems. Attacks can happen online, in-person, and via other interactions.
Scams based on social engineering are built around how people think and act. As such, social engineering attacks are especially useful for manipulating a user’s behavior. Once an attacker understands what motivates a user’s actions, they can deceive and manipulate the user effectively.
In addition, hackers try to exploit a user's lack of knowledge. Thanks to the speed of technology, many consumers and employees aren’t aware of certain threats like drive-by downloads. Users also may not realize the full value of personal data, like their phone number. As a result, many users are unsure how to best protect themselves and their information.
Generally, social engineering attackers have one of two goals:
- Sabotage: Disrupting or corrupting data to cause harm or inconvenience.
- Theft: Obtaining valuables like information, access, or money.
This social engineering definition can be further expanded by knowing exactly how it works.